
Dark data poses potentially significant risks and costs for organisations. Additionally, with an increasing focus on ESG reporting, organisations should be considering how they can measure and report on each element of ESG with respect to data being collected, generated, used and stored.
This article by Susan Bennett considers the often-overlooked energy costs of storing data, particularly as we move into the age of AI, together with the risks for organisations arising from increasing privacy and cyber security regulatory requirements. The regulatory enforcement focus on data minimisation, requires organisations to implement active data disposal and regulatory requirements to implement adequate systems and processes to protect and secure data and information. This means more than ever that organisations need to be proactive in implementing robust information and data governance and measuring the ESG of data.
The problem of dark data
Dark data is data that is collected or generated and then not utilised by the organisation. As data storage is relatively cheap compared to traditional archiving costs for hard copy records, organisations have been collecting, generating and storing exponentially increasing volumes of data. According to the Digital Decarbonisation research, up to 65% of data generated is never used and up to 15% is out of date.[I] Unless data being held is accurate, accessible and is being utilised, it is ROT. That is, data that is redundant, outdated, trivial or transitory. Data ROT poses a number of risks and potentially significant costs to organisations including:
- Data Breaches and consequent regulatory investigations and class actions arising from:
- Exposing personal data in breach of privacy regulations
- Exposing personal data, which should have been destroyed or de-identified as it was no longer required and therefore, in breach of relevant privacy regulations.
- eDiscovery costs in litigation, Royal Commission and regulatory investigations.
- Inefficiencies arising from delays for employees in identifying and accessing up-to-date and accurate data and reliable information on which to carry out their day-to-day work and for good decision-making within the organisation.
- Lack of data integrity, which may impact the quality of decision-making made at all levels within an organisation, including in AI and generative AI uses within organisations.
- Storage costs and increased energy consumption.
Data Value
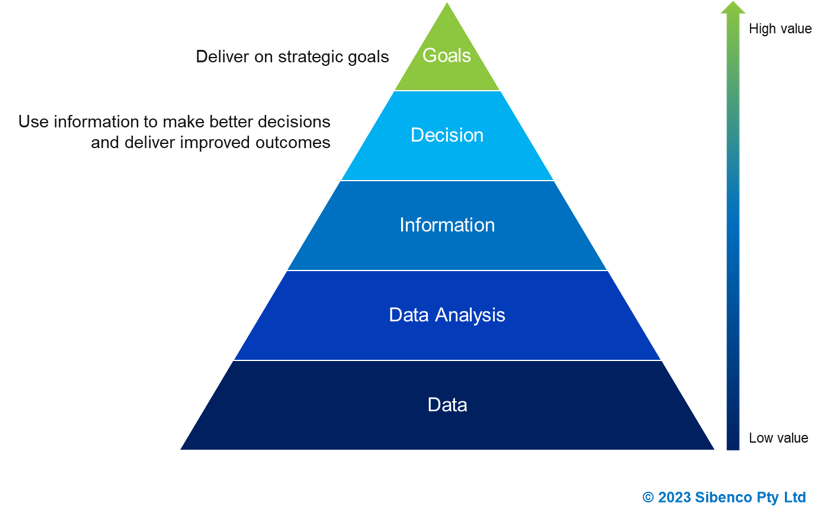
The focus on data is often discussed in terms that leads many executives and board directors to believe that data being collected and stored is or can be of value. However, decision-making or insights drawn from outdate, unreliable, or biased information is unlikely to produce any value and may give rise to legal risks and consequences. Data is of value when it is accurate, reliable and accessible and where insights and information produced from analysis enable good decisions to be made, deriving value for the organisation and ultimately delivering returns to the bottom line, as shown in the diagram below.
Figure 1 Data Value Delivering on Strategic Goals
To reduce the risks and costs arising from storing organisations, it is important that organisations implement robust information governance and robust data and information lifecycle management – read more about how to implement these in The Information Governance Primer here and the Information Lifecycle Management: what is it and how it reduces risk? here.
Figure 2 Information Lifecycle Management
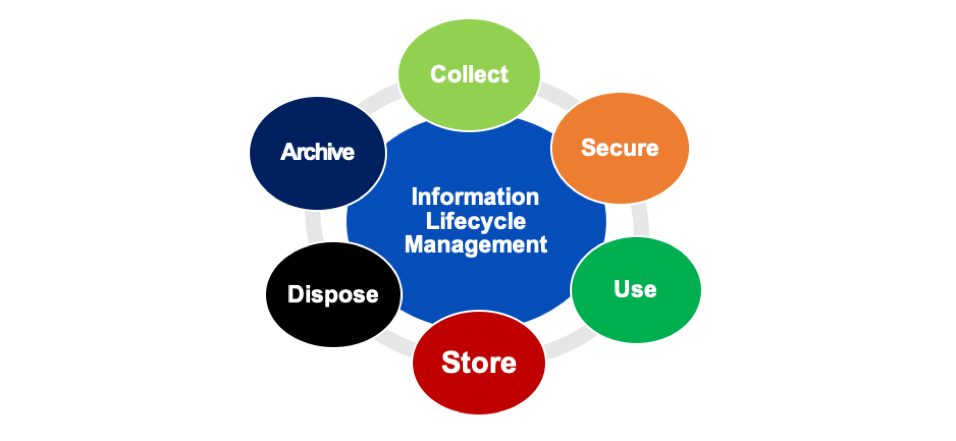
ESG risks and costs of data
Organisations need to be taking action to manage data to minimise risks and their digital carbon footprint. A report by UTS’s Institute for Sustainable Futures Institute released in July 2023 on ‘IT & Data Centre Sustainability in Australia’ has highlighted that the data centre industry is ‘exposed to significant ESG (environmental, social, and corporate governance) risks that have largely escaped our collective attention’, including the increasing need for cooling combined with huge demands for data. The report included a survey of sustainability professionals conducted between May and June 2023. The key insights from the survey included the following:[ii]
- Sustainability professionals rely on quality data to inform their actions. Only 5% of respondents felt that the quality of sustainability-related data received from Data Centre service operators was detailed. 46% of respondents were receiving no sustainability-related data. In total 59% of respondents either had insufficient, or no sustainability-related data from Data Centre service operators.
- 77% of respondents either agreed, or somewhat agreed, that organisations cannot reach their sustainability goals without significantly reducing Data Centre energy usage.
- 48% of respondents were fully aware or had some awareness of the amount of energy that data centres consume. However, 29% of respondent’s organisations did not consider Data Centre energy consumption at all. Only 22% of respondents indicated that their organisation pays sufficient attention to Data Centre energy consumption.
- 81% of respondents thought that demand for data management would increase with 21% stating it would significantly increase whereas 19% of respondents did not think demand for data management would increase.
- Over 70% of organisations surveyed had sustainability of data centres prioritised data centres in their practices, but only 9% were fully considering it. Only 15% of respondents indicated sustainability issues were a critical consideration for their organisation in procurement for Data Centre service providers.
- The most cited constraints when addressing Data Centre sustainability issues were knowledge and awareness of sustainability risks (21%), insufficient budget (18%) and poor-quality data (16%).
Energy Costs of Data Storage
The Digital Decarbonisation Project, which is funded by the UKRI National Circular Economy Research Hub and involves academics from Loughborough University states that, ‘despite the media’s focus on carbon emissions from the automotive, aviation, and energy sectors, the data industry is likely to produce more emissions than these industries combined.’[iii]
The UTS report states that currently and predicted CO2 emissions from software-related activities, account for 4-5% of global emissions. The report goes on to predict that by 2040, ‘it is estimated that software-related CO2 emissions may account for 14% of the world’s carbon footprint.’[iv] In relation to data centres and data transmission networks, the International Energy Agency reports that data centres and data transmission networks accounted for 0.9% of energy-related GHG emissions and that global data centre electricity use in 2021 was around 0.9-1.3% of global final electricity demand.’[v]
The UTS report explains that one of the major reasons why data centres use so much energy is for cooling. The report also points out that: [vi]
Ireland is now home to 25% of the data centres in Europe including newly constructed hyperscale Data centres. However, the large number of Data centres, with projections for future growth, is leading to instability in Ireland’s energy grid. According to Ireland’s Central Statistics Office electricity consumption by data centres increased by 32% in 2021. Over a six-year period to December 2021 electricity consumption by data centres increased by 265%. According to EirGrid, Ireland’s energy grid manager, by 2031, 28% of all electricity demand in Ireland is expected to come from data centres and other new large energy users. EirGrid is concerned that the growth of data centres is leading to grid instability citing the amber alerts issued in 2022.
The report also points out that the growth in use of artificial intelligence and digital currencies has the potential to increase the demand for Data Centre services.[vii]
ESG mandatory reporting for companies
Several recent developments in 2023 have highlighted that organisations need to come to grips with how they will measure ESG and be prepared to meet emerging mandatory ESG reporting requirements.
The European Union’s Corporate Sustainability Reporting Directive (CSRD (EU) 2022/2464) came into force on 5 January 2023 and introduced sustainability reporting requirements for EU companies, non-EU companies meeting certain thresholds for net turnover in the EU and companies with securities listed on a regulated EU market. Companies subject to the CSRD are required to disclose information about how sustainability-related factors, covering environmental, social and human rights and governance, affect their operations and information about how their business model impacts sustainability factors.
On 26 June 2023, the International Sustainability Standards Board (ISSB) issued its inaugural standards – IFRS S1 and IFRS S2 – for sustainability-related disclosures. They include IFRS S1 General Requirements for Disclosure of Sustainability-related Financial Information and IFRS S2 Climate-related Disclosures.
The ISSB explain that the Standards are designed to ensure that companies provide sustainability-related information alongside financial statements. The Standards have been developed to be used in conjunction with any accounting requirements.
The creation of the ISSB was announced at COP26, the 2021 UN Climate Change Conference in Glasgow, with the role of creating a global baseline for sustainability reporting. The UK government has been a strong supporter of the ISSB and is aiming to make endorsement decisions on the first 2 standards to create UK Sustainability Disclosure Standards (SDS) by July 2024.
Also in June 2023, the Chair of ASIC Joe Longo made several statements highlighting the importance of ESG reporting for listed companies in Australia including that, ‘ESG reporting is simply the next stage in a long series of important moves towards greater transparency and higher disclosure standards.’ Highlighting that ‘good disclosure depends on good governance’, Joe Longo said companies should be asking themselves:[viii]
- How can sustainability and financial reporting work together to function as an integrated whole?
- How can we ensure that marketing and advertising teams work with the legal and risk teams to ensure cohesion around sustainability-related claims?
- What assurances and processes can be put in place to ensure that the board is appropriately informed and confident about the information that is being put out?
The move towards mandatory ESG reporting, requires organisations to implement processes to ensure that the relevant and accurate data can be efficiently collected, measured and reported upon as required. This includes companies being able to identify, measure and report upon the energy costs of dark data and minimising data within the organisation. As generative AI and large language models are increasingly used within organisations the significant increase in energy consumption and environmental and social impacts (arising from the use of personal data and/or data which may be subject to copyright) should also be measured as part of the design considerations at the outset of new data-driven technology projects.
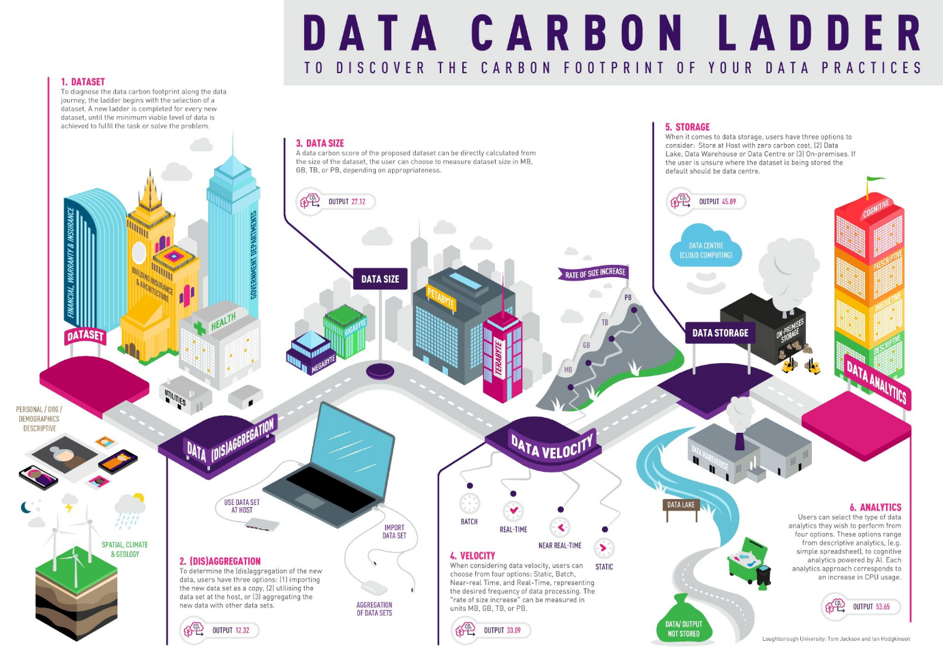
Measuring data carbon
The Digital Decarbonisation project led by academics, Professor Thomas Jackson and Professor Ian Hodkinson from Loughborough University, has designed a tool called the ‘Data Carbon Ladder’, which can be used in new data projects. The tool helps an organisation determine the appropriate size of the dataset(s) required, the optimal frequency for updates, the most suitable storage location, and the analytics necessary for a project. The Data Carbon Ladder can provide an estimated data CO2 footprint for a project, identifying areas where improvements can be made to minimise environmental impact. The Data Carbon Ladder is aimed at helping organisations make data-driven decisions, which enhance their bottom line and also align with their sustainability goals. Read more about the Data Carbon Ladder and how to use it in the article by Jackson and Hodgkinson.[ix]
The Five Essential Key Steps for Data and ESG
- A process for ensuring that the organisation has a continual and reliable mechanism for identifying data repositories and the types of data held within those repositories (the ‘Data Map’). Organisations need to understand what data they are collecting, why, and where it is being stored, including data held in third-party systems and cloud storage.
- An up-to-date Records Retention and Disposal Policy, which is enforced. This is an essential bedrock for enabling data disposal in accordance with the expiration of the retention period.
- Establish (or ensure) the Information and Data Governance Committee is overseeing the continual disposal of robust data and information lifecycle with reporting to the risk committee and/or board.
- An AI Plan and Strategy, which links the AI Framework, Information Governance Framework and the overall enterprise risks management framework. A key problem for boards and senior executives is the lack of integrated reporting in relation to data and information risks. The linking of the AI Framework and an Information Governance Framework with the enterprise Risk Management framework is essential so that boards are properly informed of the interconnected data, technology and regulatory compliance risks.
- Develop measurements for Data and an ongoing annual measurement and reporting of Data ESG criteria including:
- Auditing of data and information lifecycle in accordance with privacy, IT security, AI policies and procedures covering:
- Collection and re-use of data including personal data and applicable ethical requirements
- Privacy impact assessments, AI impact assessments, IT security impact assessments
- Costs of onsite and cloud storage (as well as the maintenance/energy and storage costs of any physical hard copy archives).
- Measuring carbon of data stored by the organisation, including data held in data stores.
- Measuring carbon for data-intensive projects, particularly projects using AI or large language models using large data sets.
- Auditing of data and information lifecycle in accordance with privacy, IT security, AI policies and procedures covering:
If you are interested in learning more about ESG and Data, join The Governance in ESG Workshop – September – InfoGovANZ
Author: Susan Bennett, LLM(Hons), MBA, FGIA, CIPP/E Founder of InfoGovANZ, Governance and Privacy Lawyer
Contact: susan.bennett@infogovanz.com
[i] Digital Decarbonisation, Costs of digitalisation to society, industry and the environment – Digital Decarbonisation
[ii] University of Technology Sydney, Institute of Sustainable Futures Report, 4
[iii] Digital Decarbonisation, Costs of digitalisation to society, industry and the environment – Digital Decarbonisation
[iv] University of Technology Sydney, Institute of Sustainable Futures Report, 6
[viii] ASIC, ASIC Chair’s AFR ESG Summit speech , 5 June 2023
[ix] Thomas Jackson and Ian Richard Hodgkinson (2023) Is there a role for knowledge management in saving the planet from too much data?, Knowledge Management Research & Practice, 21:3, 427-435, DOI: 10.1080/14778238.2023.2192580

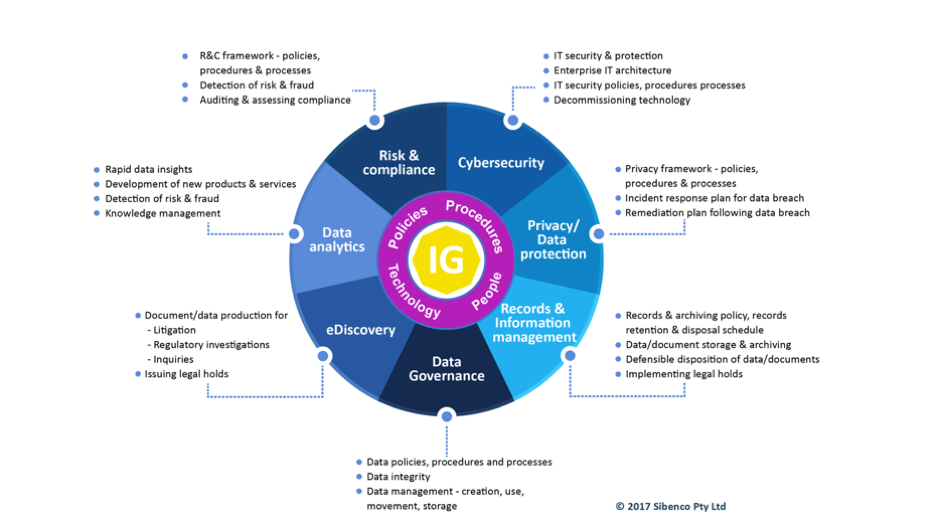
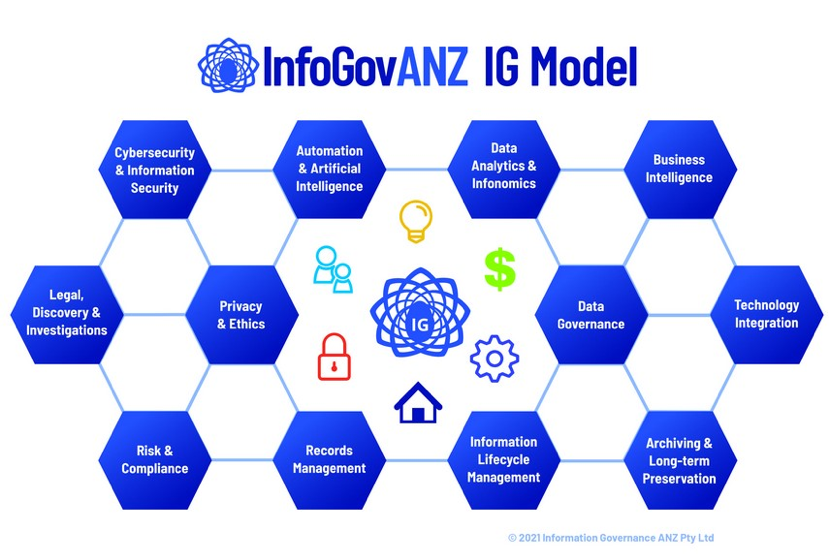


 As we put 2020 behind us and look forward to 2021, we reflected in an interactive virtual discussion forum on the key IG learnings from the past 12 months and the insights and actions we now need to be taking to make the most of the opportunities and challenges on the road to recovery in 2021.
As we put 2020 behind us and look forward to 2021, we reflected in an interactive virtual discussion forum on the key IG learnings from the past 12 months and the insights and actions we now need to be taking to make the most of the opportunities and challenges on the road to recovery in 2021.